GATE-CS-2015 (Set 1)
Question 2
Given Set A = {2, 3, 4, 5} and Set B = {11, 12, 13, 14, 15}, two numbers are randomly selected, one from each set. What is the probability that the sum of the two numbers equals 16?
Question 3
Based on the given statements, select the most appropriate option to solve the given question.
If two floors in a certain building are 9 feet apart, how many steps are there in a set of stairs that extends from the first floor to the second floor of the building?
Statements: 1. Each step is 3/4 foot high. 2. Each step is 1 foot wide.
Question 5
The number of students in a class who have answered correctly, wrongly, or not attempted each question in an exam, are listed in the table below. The marks for each question are also listed. There is no negative or partial marking.
Q.No. Marks Answered-Correctly Answered-Wrongly Not-Attempted 1 2 21 17 6 2 3 15 27 2 3 1 11 29 4 4 2 23 18 3 5 5 31 12 1What is the average of the marks obtained by the class in the examination?
Question 6
Select the alternative meaning of the underlined part of the sentence.
The chain snatchers took to their heels when the police party arrived.
Question 7
The given statement is following by some courses of action. Assuming the statement to be true, decide the correct option.
Statement: There has been a significant drop in the water level in the lakes supplying water to the city. Course of action: 1. The water supply authority should impose a partial cut in supply to tackle the situation. 2. The government should appeal to all the residents through mass media for minimal use of water. 3. The government should ban the water supply in lower areas
Question 8
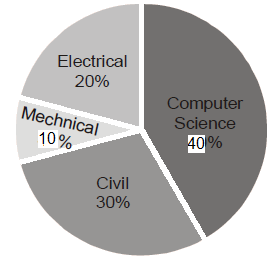
The pie chart below has the breakup of the number of students, from different departments in an engineering college for the year 2012. The proportion of male to female students in each department is 5 : 4. There are 40 males in Electrical Engineering. What is the different between the numbers of female students in the Civil department and the female students in the Mechanical department?

Question 9
The probabilities that a student passes in Mathematics, Physics and Chemistry are m, p and c respectively. Of these subjects, the student has 75% chance of passing in at least one, a 50% chance of passing in at least two and a 40% chance of passing in exactly two. Following relations are drawn in m, p and c:
1. p + m + c = 27/20 2. p + m + c = 13/20 3. (p) × (m) × (c) = 1/10
Question 10
Match the following
List-I List-II A. Condition coverage 1. Black-box testing B. Equivalence class partitioning 2. System testing C. Volume testing 3. White-box testing D. Alpha testing 4. Performance testing Codes: A B C D (a) 2 3 1 4 (b) 3 4 2 1 (c) 3 1 4 2 (d) 3 1 2 4
There are 65 questions to complete.
Last Updated :
Take a part in the ongoing discussion