GATE-CS-2016 (Set 1)
Question 1
Out of the following four sentences, select the most suitable sentence with respect to grammar and usage.
Question 3
Archimedes said, “Give me a lever long enough and a fulcrum on which to place it, and I will move the world.” The sentence above is an example of a ___________ statement.
Question 4
If ‘relftaga’ means carefree, ‘otaga’ means careful and ‘fertaga’ means careless, which of the
following could mean ‘aftercare’?
Question 5
A cube is built using 64 cubic blocks of side one unit. After it is built, one cubic block is removed from every corner of the cube. The resulting surface area of the body (in square units) after the
removal is __________.
Question 6
A shaving set company sells 4 different types of razors, Elegance, Smooth, Soft and Executive. Elegance sells at Rs. 48, Smooth at Rs. 63, Soft at Rs. 78 and Executive at Rs. 173 per piece. The table below shows the numbers of each razor sold in each quarter of a year.
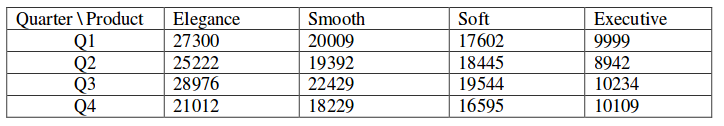 Which product contributes the greatest fraction to the revenue of the company in that year?
Which product contributes the greatest fraction to the revenue of the company in that year?
 Which product contributes the greatest fraction to the revenue of the company in that year?
Which product contributes the greatest fraction to the revenue of the company in that year?
Question 7
Indian currency notes show the denomination indicated in at least seventeen languages. If this is not an indication of the nation’s diversity, nothing else is.
Which of the following can be logically inferred from the above sentences?
Question 8
Consider the following statements relating to the level of poker play of four players P, Q, R, and S.
I P always beats Q II. R always beats S III. S loses to P only sometimes IV. R always loses to QWhich of the following can be logically inferred from the above statements?
(i) P is likely to beat all the three other players (ii) S is the absolute worst player in the set
Question 10
In a process, the number of cycles to failure decreases exponentially with an increase in load. At a load of 80 units, it takes 100 cycles for failure. When the load is halved, it takes 10000 cycles for failure. The load for which the failure will happen in 5000 cycles is ________.
There are 65 questions to complete.
Last Updated :
Take a part in the ongoing discussion